Case study – preventing Malgent trojan horse
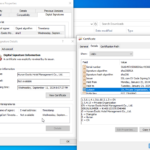
Intro Yesterday (September 12th, 2024) our Active Endpoint Deception platform prevented a new variant of Malgent trojan horse that was built just a few hours prior to the attack on

Intro Yesterday (September 12th, 2024) our Active Endpoint Deception platform prevented a new variant of Malgent trojan horse that was built just a few hours prior to the attack on

As technology evolves, so do the tactics of cybercriminals. Large Language Models (LLMs) like GPT-4, designed to assist in various legitimate tasks, are being increasingly exploited by threat actors to

Background We previously covered DLL Hijacking when we discovered extensive vulnerabilities in .NET, which potentially open any .NET application to such attacks. Additionally, this is not the first time that
Deceptive Bytes’ research team detected in recent days a wave of attacks on European organizations, while the attacks are not that sophisticated, they employ social engineering to make users run

Every day, all around the world, malware is attacking organizations and businesses from all sizes, affecting their day-to-day activities and causing businesses losses which can be significant. When you think

There are many injection techniques used by malware authors, from simply calling CreateRemoteThread to advance ones like AtomBombing, PROPagate & others. How basic DLL injections work? Usually when a malware

Artificial Intelligence (AI) and Machine Learning (ML) are considered the next evolution in computer science as they allow computers to perform complex decisions and tasks that were up until now

The new year is around the corner and as we prepare for it, we wanted to take a look at what we should expect, here are some of our predictions

In our last two posts we’ve shown how vendors like Symantec and Microsoft (among others) miss detecting threats due to the nature of how their engines operate. So how do