2025 in numbers
Ransomware in 2025 hit a new peak in volume while becoming less profitable for attackers, with more organizations refusing to pay and focusing on recovery and resilience instead. At the same time, industrial, services, healthcare, and public-sector victims saw longer disruptions and higher recovery costs, keeping ransomware one of the most damaging threats on the enterprise risk register.
2025 in numbers
-
Global confirmed ransomware incidents reached roughly 4,700+ cases by Q3 2025, about a 30–35% jump versus 2024, marking a new high in observed activity.
-
Yet total ransomware revenue dropped by more than one-third year over year, with payment rates falling to around 1 in 4 victims paying, an all‑time low in many datasets.
-
Average operational disruption lasted about 24–27 days per attack, and all‑in incident costs (forensics, downtime, rebuilds, reputational damage) often reached USD 5–6M per case, even when ransoms were not paid.
These numbers show a pivot: ransomware is shifting from being primarily a “quick cash” operation to a broader business‑disruption and extortion weapon.
Who attackers hit in 2025
Multiple industry analyses point to a concentration of attacks on manufacturing, services, healthcare, financial, and government organizations.
-
Manufacturing and industrial: Several reports place manufacturing and industrial operators among the most targeted sectors, with some datasets showing them at or near the top of the victim count.
-
Services and professional firms (IT, legal, consulting, real estate) made up a large share of leak‑site victims in Q2 2025, with “services” alone accounting for over 40% of posted victims in one analysis.
-
Healthcare continued to experience high‑impact incidents, including multi‑million‑dollar recovery costs and patient‑safety concerns, keeping it one of the most sensitive verticals for ransomware.
-
Government and education stayed high on the target list due to data sensitivity, under‑resourced defenses, and the operational pressure to restore citizen or student services quickly.
- Ransomware victims by sector, 2025
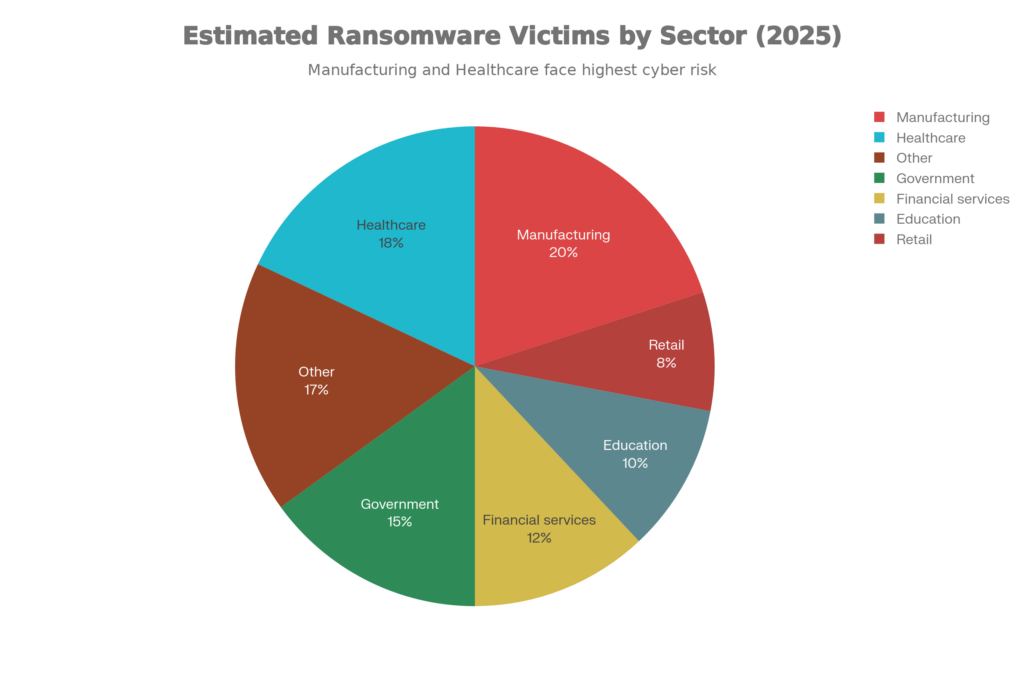
Ransomware continued to heavily impact manufacturing, healthcare, and government organizations in 2025
- Global confirmed incidents 2020–2025
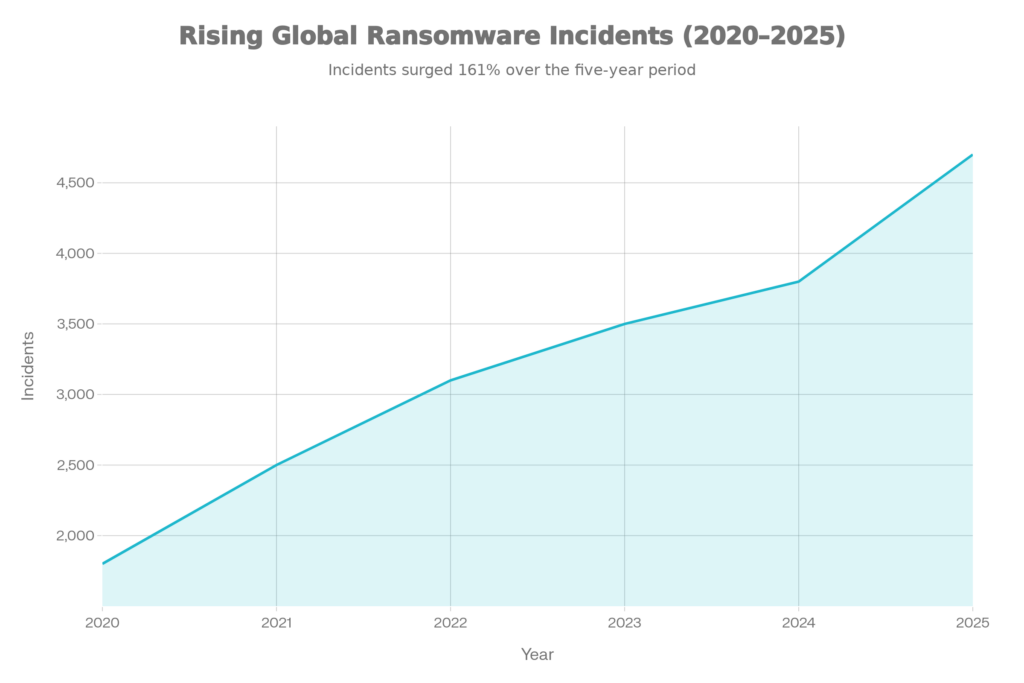 Confirmed ransomware incidents have increased sharply since 2020, with a notable spike in 2025
Confirmed ransomware incidents have increased sharply since 2020, with a notable spike in 2025
Tactics, groups, and technical shifts
Attacker behavior in 2025 continued trends from previous years while adding more automation and multi‑layered extortion.
-
Double and triple extortion as the norm
-
Encryption plus data theft, public leak‑site shaming, DDoS pressure, and direct outreach to customers or partners increasingly became standard playbooks.
-
Many cases in 2025 show that even when organizations restored from backups, attackers still tried to monetize via data‑leak threats and reputational damage.
-
-
RaaS (Ransomware‑as‑a‑Service) and affiliate ecosystems
-
Mature RaaS programs continued to dominate, with well‑known families such as LockBit, Clop, and others (plus emerging brands) remaining in the top‑tier of observed incidents.
-
Law‑enforcement pressure and takedowns caused periodic dips or re‑brands, but the underlying affiliate model—separating access brokers, operators, and negotiators—stayed resilient.
-
-
AI‑assisted operations and automation
-
Several 2025 threat reports highlight adversaries using automation and AI to speed up reconnaissance, vulnerability discovery, target selection, and phishing customization.
-
Combined with botnets and mass exploitation of exposed services, this drove a cadence where one analysis estimated an organization somewhere faces a ransomware attempt roughly every tens of seconds globally.
-
-
Attack vectors remain familiar, but scaled
-
Top entry points stayed consistent:
-
Phishing and social engineering.
-
Exploitation of unpatched vulnerabilities in internet‑facing systems and widely used software.
-
Compromised remote access services and credential theft.
-
-
What changed in 2025 was less “what” and more “how fast and at what scale” these vectors were exploited.
-
Defensive lessons
-
Assume compromise of perimeter and identity
-
With initial access commoditized, defenses must treat endpoint and workload execution as the last practical control point.
-
Controls that can inspect and stop malicious behaviors within seconds of execution drastically reduce the chance an incident escalates to encryption or data theft.
-
-
Design for fast containment, not just backup
-
Backups and DR are necessary but no longer sufficient when data theft and extortion are involved.
-
2025 incidents show that organizations with robust segmentation, least‑privilege, and automated isolation (host‑level or network‑level) limited blast radius and reduced downtime.
-
-
Reduce human‑in‑the‑loop dependencies
-
Many of the most damaging incidents still occurred on nights, weekends, or holidays, when response coverage is thin.
-
Automated prevention, policy‑driven blocking, and real‑time anomaly or behavior controls are critical so that protection does not depend on an analyst noticing an alert in time.
-
-
Measure success by avoided impact, not just blocked samples
-
Given that payment rates are falling but downtime and costs remain high, programs need to track “time to prevent” and “time to contain” alongside classic MTTR or detection metrics.
-
The takeaway for security teams in 2026:
Detection and backup alone are not enough when attackers can move from initial access to encryption and data theft in minutes. Pre‑execution controls on endpoints and servers—stopping ransomware within 1–2 seconds—are what keeps downtime, extortion, and business disruption off the table
Don’t Miss a Thing
Sign up today and we’ll send an email when new posts come out.
We collect and use this information in accordance with our privacy policy.